2013 Snowden Documents Were Forgery
From the moment Edward Snowden fled to Hong Kong, China, with a trove of top-secret documents, the Obama–Biden administration was complacent about espionage and the use of forged documents
Main Points
● 2013 Snowden allegations about Internet surveillance were entirely false and backed by forged documents
● Snowden stole and delivered to a foreign (likely Russian) intelligence more than a million secret military, NSA, and CIA documents
● Smearing the NSA and compromising the US tech industry was part of the foreign intelligence operation
● Snowden continued aiding Russian intelligence while living in Russia
● The Obama–Biden administration was covertly aiding Snowden since he fled the US
● Its complacency towards Snowden and Russian government espionage has contributed to suspicions against … Donald Trump!
Introduction
Snowden stole the “keys to the kingdom”
In 2013, Edward Snowden stole and transferred over a million electronic documents of the US Department of Defense and the US intelligence community to the Russian government. Many stolen documents contained Top Secret Sensitive Compartmented Information. That included what the NSA called the “keys to the kingdom.” Many, if not all, of these documents were likely also shared with the government of China. This espionage caused enormous damage to the US. See the Congressional Report, declassified in 2016, and Epstein, Edward Jay, How America Lost Its Secrets: Edward Snowden, the Man and the Theft, 2017, Kindle Edition (“EEJ”). EEJ might be the best-researched book on the Snowden affair.
Snowden’s domestic surveillance allegations were bogus
Snowden claimed to be a whistleblower by inventing a domestic surveillance scandal to distract from this espionage. However, Snowden’s domestic surveillance “revelations” were entirely false and backed by forged documents.
Almost everything Snowden said publicly was a lie. Most of what the mainstream media has told us about him is a lie. He was not a genius hacker but a dorky high-school dropout with ambitions of becoming a male model. Before working for the NSA, he worked as a system administrator at the CIA, where his duties were described as “moving files” to a backup location. Snowden obtained a job at the CIA through nepotism (EEJ, p. 32). Snowden had not completed training at his new NSA position when he absconded with documents of enormous importance, which had nothing to do with any allegations of mass surveillance (EEJ, p. 176). How was he able to do this?
“When you look at the totality of Snowden’s actions certainly one hypothesis that jumps out at you, that seems to explain his ability to do all these things, is that he had help and had help from somebody who was very competent in these matters. —GENERAL MICHAEL HAYDEN, former director, NSA and CIA” - (EEJ, p. 184)
False Claims and Forged Documents
False News
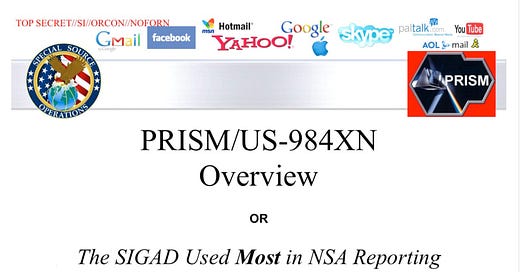
On June 6, 2013, The Guardian wrote, “Top-secret Prism program claims direct access to servers of firms including Google, Apple and Facebook,” and accompanied this claim with slides from a purported top-secret PRISM presentation. The Guardian used to be partly funded by the British government. The Washington Post (“WaPo”) published a similar article almost simultaneously. The central allegation was that the US government was engaged in unconstitutional domestic surveillance on the Internet and was helped by leading tech companies.
That allegation was false. The purported NSA PRISM presentation is a crude forgery.
The presentation’s content and design reveal the purpose of supporting the allegations made by The Guardian and WaPo, and it is not consistent with training or other internal purposes. The presentation’s security marking is incorrect. Only 11 purported slides out of the alleged 41 were unveiled and not in their original form. Most likely, the purported PRISM slides were manufactured by The Guardian because it vouched for its authenticity. Further, the logo seems inspired by another PRISM – “Parameter-elevation Regressions on Independent Slopes Model” – a meteorological program at Oregon State University.
The allegations by The Guardian and WaPo were immediately and strongly rebutted by all the tech companies and government officials. Apple’s statement in Google, Facebook, Dropbox, Yahoo, Microsoft, Paltalk, AOL And Apple Deny Participation In NSA PRISM Surveillance Program is representative: “We have never heard of PRISM. We do not provide any government agency with direct access to our servers, and any government agency requesting customer data must get a court order.” Top executives and founders of big-tech companies reaffirmed those denials and have never withdrawn them. On the government side, the ODNI stated: “PRISM is not an undisclosed collection or data mining program. It is an internal government computer system …”. This statement was confirmed independently (1, 2). Many things are abbreviated as PRISM, and the word ‘program’ has multiple meanings.
Technical Aspects of Internet Surveillance
Internet traffic is public. The traffic consists of data packets. Each packet is like a postcard rather than a letter in an envelope. Packets traverse routers owned by different entities. Everyone with access to any router can read and record unencrypted traffic. To protect users’ privacy, most web servers use encryption. Neither government nor private parties can break this encryption. The IP addresses are generally visible to third parties but are metadata. Also, individuals can use VPNs or proxy servers to hide their IP addresses. Individuals can also avoid using unencrypted websites and other programs that do not encrypt data before sending it over the Internet. Also, we should be able to ensure that the information that we send or receive over the Internet does not cross the border. We cannot do that because of Obamanet regulations.
The NSA collected only publicly visible data (or just metadata) that crossed US borders or was entirely exchanged abroad. The federal government's constitutional powers are maximal at the border. The failure to protect the US borders in cyberspace has been a continuing US government blunder for the last 20 years. Only the “no border, no wall, no USA at all” crowd could demand that the government not secure the border in cyberspace.
The collected data or metadata went into a database with very restricted access. Although this data or metadata was obtained without violating the IV Amendment or other Constitutional restrictions, it was not treated as government property. To get anything from that database, the FBI and the intelligence community had to query that database under the rules of Section 702 of FISA. Querying that database required justification, minimization, and masking of US persons. There was congressional and other oversight.
This two-step process is frequently misunderstood. Querying the NSA database is misrepresented as a primary collection. When Snowden said, "I, sitting at my desk, had the authority to wiretap anyone, from you or your accountant to a federal judge to even the president,” he was lying.
Read PRISM Isn’t Data Mining and Other Falsehoods in the N.S.A. “Scandal”.
The Obama–Biden administration was complacent and, possibly, complicit
Obama Administration’s Left-Wing Sympathy to Snowden
The Obama–Biden administration's left wing was on Snowden’s side. In January 2014, Obama’s “wingman,” AG Eric Holder, showed a unique inclination toward Snowden by offering him negotiations while Snowden was in Moscow. In 2016, he stated that Snowden had performed a public service. This was his “public service”:
“The classified DIA report showed that Snowden took “over 900,000” military files from the Department of Defense in addition to the NSA files he had taken. The Defense Department loss in terms of the number of files stolen actually exceeded the loss—in sheer numbers—of NSA documents.” – EEJ, pp. 158-159
“[per David Leatherwood, DIA] the military files compromised by Snowden included documents bearing on military plans and weapons systems; foreign governments’ intelligence activities (including special activities), intelligence sources, or methods of cryptology; scientific and technological matters relating to national security; and vulnerable systems, installations, infrastructures, projects, plans, and protection services related to national security and the development, production, or use of weapons of mass destruction.” – EEJ, p. 161
Obama’s Failure to Confront Lies and Forgeries
The Obama–Biden administration did not publicly reveal that The Guardian–WaPo “documents” were fabrications, nor did the administration insist that Snowden’s words were a lie.
Obama’s Failure to Have Snowden Extradited
The Obama–Biden administration had an opportunity to have Snowden extradited from Hong Kong. An extradition treaty existed and had always been honored. China had the right to veto but could not use it for political reasons: Xi Jinping was meeting Obama in California on June 8, 2013. Snowden was tracked down in Hong Kong on June 8, and there was plenty of time to request and obtain his extradition.
When the extradition paperwork was sent on June 16, his name was misspelled, and it was returned on that technicality. The misspelling of his middle name "James instead of Joseph” (EEJ, p. 178) was likely intentional.
Obama’s Sabotage of US Tech
At one point, the false allegations of mass surveillance aided by tech companies became mixed up with perfectly legal and constitutional individual court warrants and national security letters, the latter requesting only metadata (not the content).
The Obama–Biden administration did not tell the public how few warrants and national security letters were sent to tech companies. It prohibited tech companies from revealing anything about this number, even the order of magnitude, even with a delay. In 2012, Google received less than 2,000 warrants concerning less than 25,000 accounts. According to knowledgeable people, most of them were in connection with local crimes. Compare that to over 200,000 robberies that were happening in the US annually.
Withdrawing this information suggested that the number of warrants and affected accounts was much higher, possibly approaching blanket surveillance. That barred the tech companies from defending themselves and the US in the court of public opinion. In hindsight, it looks like intentional sabotage of the national security community by the left wing of the Obama–Biden administration.
Obama and Booz Allen Hamilton
The NSA hired Snowden as a contractor through Booz Allen Hamilton. After Snowden’s theft, the Obama–Biden administration did not punish Booz Allen, did not terminate relationships with it, and not increase scrutiny of its contractors. Another Booz Allen NSA contractor was busted for stealing secret documents in 2016 (EEJ, p. 270), but Booz Allen's government business grew between 2013 and 2016. Even political donations of Booz Allen managers (5:1 in favor of Democrats in 2012) cannot explain that.
Discreditation of the NSA
At the time of the Soviet Union, “the KGB had organized press conferences for all the previous NSA defectors.” (EEJ, p. 204). Those defectors also claimed to be whistleblowers (EEJ, pp. 275-276). Russia is not the Soviet Union, but some practices were re-adopted. It is reasonable to conclude that damaging the reputation of or even destabilizing the NSA was part of the Snowden operation. By failing to have Snowden extradited or, at least, his lies debunked, the Obama–Biden administration aided Russian intelligence in this task and consequent use of Snowden as an asset.
Some Consequences
Alienation of Constitutionalists, Libertarians, and Tech Workers
The Guardian – WaPo – Russian intelligence operation, aided by the Obama–Biden administration, alienated large and essential segments of the public from the national security and intelligence community. The public believed Snowden more than routine denials from the government. Many people started believing in total government surveillance. Strict constitutionalists and libertarians were the first to condemn one of the most harmless government agencies for something it did not do. Many tech workers become hostile to national security interests.
This weakened the NSA and the FBI in cyberspace and caused the loss of defensive knowledge and capacities, not only intelligence capabilities. That enabled the cyber components of the Russia hoax of 2016. The hoax supporters in the intelligence community have further perverted cybersecurity knowledge and practice, and this problem has been only growing.
Snowden continued to speak for Russian intelligence[1]
From October 2013 through 2014, the German press published multiple claims of US espionage against Germany, supposedly based on a small batch of documents Snowden gave journalists in Hong Kong, China,[2] not to be confused with the million-plus documents he took to Russia. One of the most damaging was the allegation that the US bugged the phone of the German Chancellor Angela Merkel and was eavesdropping on her conversations. The US immediately denied these allegations. These claims were supported only by invoking Snowden’s archive and his speech from Moscow.[3] These allegations sparked mistrust between the US and Germany and other European Union countries at the time when Russia seized and annexed Crimea. In 2015, a German investigation concluded the allegations were false and were not even based on any materials from Snowden’s archive. Some people said that “this material was released at the behest of the Russian intelligence service” (EEJ, p.230), although fake news journalists could have invented it without any evidence.
The Wikileaks Connection
In 2012, WikiLeaks collaborated with and received money from the Russian government, including in connection to WikiLeaks’ movie Mediastan (EEJ, p.126). WikiLeaks’ Sarah Harrison led this activity. She also arrived in Hong Kong and attempted to aid Snowden and his handlers by diverting attention from his intent to fly to Russia (EEJ, p.128). On June 23, she flew with Snowden to Moscow. Then she stayed with him in the Sheremetyevo airport, taking part in the show designed to convince naïve people that Snowden had no connection to Russian intelligence (EEJ, pp.228-229).
2016 Russia Hoax Connections
Many national security officials could see that WikiLeaks was connected to Russian intelligence, even as the Obama–Biden administration was trying to hide that. Based on this and certain other cases, they could have concluded that the intelligence community developed a blind spot regarding Russian government activities in the US. When the DNC dirty laundry started to appear on WikiLeaks courtesy of DNC insiders (maybe Seth Rich), they could suspect the Kremlin behind it. The DNC insiders and ordinary Americans who transferred information to WikiLeaks were almost certainly unaware of the prior connections between WikiLeaks and Russian intelligence, but “Generals always fight the last war.”
Technical Evidence of Forgery
General
The content of the purported PRISM presentation has been proven false. Additionally, the purported presentation has incorrect security markings. In addition, its design and content reflect the intent to accuse the leading tech companies and the NSA of illegal surveillance rather than the purported intent to train its readers. WaPo has stealthily revised its PRISM article after its publication, removing parts consistent with the purported presentation. The Guardian claimed it had verified the authenticity of the PRISM presentation. This was a lie. The design and font of the purported PRISM presentation look lifted from a meteorological PRISM program of Oregon State University.
The Purported Content Reveals the Author’s Intent
“I thought it was a joke at the beginning, like a caricature of an overly corporate slide template,” said one designer after seeing the purported presentation. This is because cheap forgery looks like a caricature.
Immediately after the publication of the allegations by the Guardian and the Washington Post, supported by the New York Times, knowledgeable people pointed to the inauthenticity of the PRISM presentation. Others suggested the whole reporting was a hoax. But the righteous outrage felt good, so many people chose not to allow facts to confuse themselves.
The language and content of the presented slides reveal the intent to deliver the (dis)information that Snowden and the Guardian–WaPo needed to manufacture a scandal. This is supposed to be a training presentation, but there is very little useful for training. This is why the common header contains 13 logos. That does not make sense because the names of companies are supposed to change as the program grows.
Incorrect Security Marking
At the relevant time, the classification goals and procedures were determined by Executive Order 13526 from 2009. The main thrust of this order was to avoid excessive classification and make declassification easy. Among its requirements is the individual marking of each page and slide and portion marking – separately marking each document element (including a heading, a figure, a table, and even line items), which might have a classification lower than the whole page.
Classification marking was regulated by multiple documents issued by NARA and intelligence agencies. Some of the most relevant documents were the Intelligence Community Authorized Classification and Control Markings Manual (“CAPCO”, 2011–2012), NSA/CSS Policy Manual 1-52 (“NSA/CSSM 1-52”, November 16, 2012), and National Archives Information Security Oversight Office rules (2010). These documents were publicly available.
Slide 1 from the purported PRISM presentation
(1) Multiple errors in the classification authority block. It appears on the first slide as a red stamp, saying:
“Derived From: NSA/CSSM 1-52
Dated: 20070108”
NSA/CSSM 1-52 is an unclassified classification manual. A top-secret document cannot derive information from it. Based on the content of the purported presentation, this line had to be “Derived From: Multiple Sources”. See NSA/CSSM 1-52, p.21.
The purported presentation is dated April 2013. The relevant NSA/CSSM 1-52 went into force on November 16, 2012, superseding one from January 8, 2007. Thus, if an NSA official made a mistake by referring to the manual instead of the sources, s/he would have referred to it: “Dated: 20121116”.
The likely cause of these mistakes is that the individual manufacturing this “document” just looked at examples found on the Internet. Many unclassified documents online, especially samples, have this “Derived From: NSA/CSSM 1-52” line. Most documents available on the Internet in June 2013 were created when the 2007 version was in effect, so they reference it.
The banner line (“TOP SECRET//SI//ORCON//NOFORN”) is placed incorrectly in most slides. The rules say: “The banner line must be conspicuously placed at the top and bottom (header and footer) of each page, in a way that clearly distinguishes it from the informational text …” (CAPCO, p.18). In the purported presentation, the top banner line blends with the companies’ logos instead of being above them. The bottom banner line is partially obscured on slide 7 and is inside the content on slide 9.
One can see the banner line in other declassified or leaked documents (e.g., 1, 2).
(2) Alleged presentation violates other marking rules. For example, slide 2 contains only public information but is marked as top secret. Excessive classification would have been a serious offense.
(3) Portion marking is not applied.
The original PRISM is the “Parameter-elevation Regressions on Independent Slopes Model”
There was an Oregon State Climate Group project named PRISM: “PRISM data sets were developed through projects funded partly by the USDA Natural Resources Conservation Service, USDA Forest Service, NOAA Office of Global Programs, and others.” The federal government funded this PRISM and assembled massive datasets – about the weather. It was unrelated to the NSA or FBI.
The name and font are identical to the one used in the purported NSA PowerPoint presentation, except for size and proportions; even the white color matches. It is possible that the fabricators lifted this word straight from the original image on the Oregon State website and combined it with an optical prism clipart. Both logos feature a rainbow and triangles.
(1) A fragment from the Oregon University website
(2) The image with the word “PRISM” and transparency from that fragment
(3) The Guardian-WaPo logo, using the word “PRISM” from this image with changed size and proportions
The Purported Presentation is Incomplete
Only 11 slides (out of 41 claimed) were published by The Guardian and WaPo together. These slides were published over several days; the latter could have incorporated feedback from the earlier ones. There were some differences between the slides, which the Guardian claimed were caused by different software used to convert the original PowerPoint slides to PDF, but no original slides were published.
Remarks
Phone Calls Metadata was the Exception
This article is about the allegations of Internet surveillance, which were the leading cause of the scandal. It does not cover the bulk metadata collection on domestic phone calls, which was old news and settled law. This collection started long before 9/11. Metadata does not include the content. The Supreme Court determined that this metadata was classified as the business records of the phone companies rather than private information (Smith v. Maryland, 1979). Access to these records was minimized to protect privacy and many levels of oversight. A FISA Court order concerning Verizon Business and the phone metadata was the only authenticated document linked to Snowden.
The Espionage Story
What happened before Snowden popped up in Hong Kong, China, is out of the scope of this paper. The only relevant point is that the “official” story he and his media enablers have told does not make sense. It is impossible. That means it is just a cover story, the purpose of which is to conceal the truth.
Books
Cliff Kincaid and Edward Lucas also wrote unflattering books about Snowden.
“Lt. Gen. Ion Mihai Pacepa, the highest-ranking Soviet bloc intelligence official ever to defect to the West, said he believed that Snowden “is an agent of the Russian foreign intelligence service.”” - Kincaid, Cliff. Blood on His Hands: The True Story of Edward Snowden, 2015 (“CK”)
“Official responses to the Snowden revelations have been lame. The White House blames the NSA for allowing the documents to leak; its rebuttals to the claims made have been laconic and dutiful, rather than vigorous.” - Lucas, Edward. The Snowden Operation: Inside the West’s Greatest Intelligence Disaster, 2014 (“EL”)
“The next oddity is that he left his job in Japan in September 2010 and visited India for a week, ostensibly to attend a four-day course on ethical hacking. India is far friendlier territory for Russian spies wanting to talk to a source than somewhere like Japan” – EL.
One could take such a course over the Internet.
Articles
The real story in the NSA scandal is the collapse of journalism, June 8, 2013 (emphasis added):
“A bombshell story published in the Washington Post this week alleged that the NSA had enlisted nine tech giants, including Microsoft, Google, Facebook, and Apple, in a massive program of online spying. Now the story is unraveling, and the Post has quietly changed key details. …
One day later, with no acknowledgment except for a change in the timestamp, the Post revised the story, backing down from sensational claims it made originally. But the damage was already done. … If you followed the link to that story … you found a completely different had been stripped of key details, with no acknowledgment of the changes”
What is known about NSA's PRISM program, 2014 updated in 2022: the author has subject matter knowledge but is naïve.
[1] “ “No country, not even the United States, would grant sanctuary to an intelligence defector who refused to be cooperative,” answered a former CIA officer who had spent a decade dealing with Russian intelligence defectors. “That’s not how it works.” If so, it seems plausible to believe that, as Kucherena said, the documents Snowden brought to Russia explain why Russia exfiltrated him from Hong Kong and provided him with a safe haven.” - EEJ, p. 219
[2] “Research by SPIEGEL reporters in Berlin and Washington, talks with intelligence officials and the evaluation of internal documents of the US' National Security Agency and other information, most of which comes from the archive of former NSA contractor Edward Snowden , lead to the conclusion that the US diplomatic mission in the German capital has not merely been promoting German-American friendship. On the contrary, it is a nest of espionage. … The NSA spying scandal has thus reached a new level, becoming a serious threat to the trans-Atlantic partnership. The mere suspicion that one of Merkel's cellphones was being monitored by the NSA has led in the past week to serious tensions between Berlin and Washington.” - https://www.spiegel.de/international/germany/cover-story-how-nsa-spied-on-merkel-cell-phone-from-berlin-embassy-a-930205.html
[3] “It was also clear that Snowden gave credence to the release in Moscow. He made a major point about the hacking of Merkel’s phone in an interview with Wired in 2014. Just about two weeks before the leak, Kucherena [Snowden’s Russian government attorney] said Snowden still had access to the documents. Clearly, someone had access. But whoever was behind it, the release of information about the alleged bugging of Merkel’s phone resulted in badly fraying U.S. relations with Germany in the midst of developing troubles in Ukraine. As it later turned out, according to the investigation of the German federal prosecutor, which concluded in 2015, there was no evidence found in this document, or elsewhere, that Merkel’s calls were ever actually intercepted.” - EEJ, p. 231